 |
miasm
Reverse engineering framework
|
 |
miasm
Reverse engineering framework
|
Public Member Functions | |
| def | __init__ (self, base, expr_simp=expr_simp_explicit) |
| def | base (self) |
| def | mask (self) |
| def | __contains__ (self, offset) |
| def | __getitem__ (self, offset) |
| def | __setitem__ (self, offset, value) |
| def | __delitem__ (self, offset) |
| def | __iter__ (self) |
| def | __len__ (self) |
| def | __repr__ (self) |
| def | copy (self) |
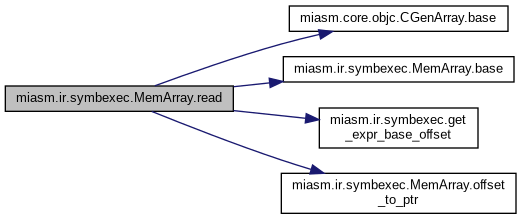
| def | read (self, offset, size) |
| def | write (self, offset, expr) |
| def | memory (self) |
| def | dump (self) |
Static Public Member Functions | |
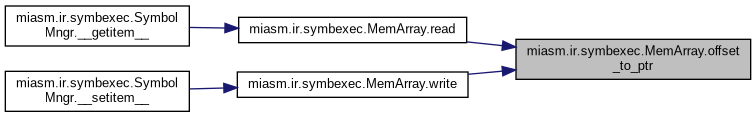
| def | offset_to_ptr (base, offset) |
Public Attributes | |
| expr_simp | |
Link between base and its (offset, Expr) Given an expression (say *base*), this structure will store every memory content relatively to an integer offset from *base*. The value associated to a given offset is a description of the slice of a stored expression. The slice size depends on the configuration of the MemArray. For example, for a slice size of 8 bits, the assignment: - @32[EAX+0x10] = EBX will store for the base EAX: - 0x10: (EBX, 0) - 0x11: (EBX, 1) - 0x12: (EBX, 2) - 0x13: (EBX, 3) If the *base* is EAX+EBX, this structure can store the following contents: - @32[EAX+EBX] - @8[EAX+EBX+0x100] But not: - @32[EAX+0x10] (which is stored in another MemArray based on EAX) - @32[EAX+EBX+ECX] (which is stored in another MemArray based on EAX+EBX+ECX)
| def miasm.ir.symbexec.MemArray.__init__ | ( | self, | |
| base, | |||
expr_simp = expr_simp_explicit |
|||
| ) |
| def miasm.ir.symbexec.MemArray.__contains__ | ( | self, | |
| offset | |||
| ) |
| def miasm.ir.symbexec.MemArray.__delitem__ | ( | self, | |
| offset | |||
| ) |
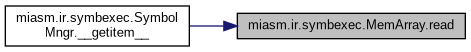
| def miasm.ir.symbexec.MemArray.__getitem__ | ( | self, | |
| offset | |||
| ) |
| def miasm.ir.symbexec.MemArray.__iter__ | ( | self | ) |
| def miasm.ir.symbexec.MemArray.__len__ | ( | self | ) |
| def miasm.ir.symbexec.MemArray.__repr__ | ( | self | ) |
| def miasm.ir.symbexec.MemArray.__setitem__ | ( | self, | |
| offset, | |||
| value | |||
| ) |
| def miasm.ir.symbexec.MemArray.base | ( | self | ) |
Expression representing the symbolic base address
| def miasm.ir.symbexec.MemArray.copy | ( | self | ) |
Copy object instance
| def miasm.ir.symbexec.MemArray.dump | ( | self | ) |
Display MemArray content
| def miasm.ir.symbexec.MemArray.mask | ( | self | ) |
Mask offset
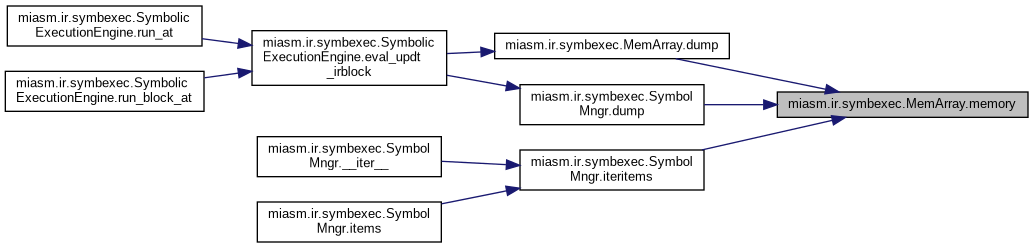
| def miasm.ir.symbexec.MemArray.memory | ( | self | ) |
Iterate on stored memory/values The goal here is to group entities. Consider the following state: EAX + 0x10 = (0, EDX) EAX + 0x11 = (1, EDX) EAX + 0x12 = (2, EDX) EAX + 0x13 = (3, EDX) The function should return: @32[EAX + 0x10] = EDX
|
static |
Return an expression representing the @base + @offset @base: symbolic base address @offset: relative offset integer to the @base address
| def miasm.ir.symbexec.MemArray.read | ( | self, | |
| offset, | |||
| size | |||
| ) |
Return memory at @offset with @size as an Expr list @offset: integer (in bytes) @size: integer (in bits), byte aligned Consider the following state: - 0x10: (EBX, 0) - 0x11: (EBX, 1) - 0x12: (EBX, 2) - 0x13: (EBX, 3) A read at 0x10 of 32 bits should return: EBX
| def miasm.ir.symbexec.MemArray.write | ( | self, | |
| offset, | |||
| expr | |||
| ) |
Write @expr at @offset @offset: integer (in bytes) @expr: Expr instance value
| miasm.ir.symbexec.MemArray.expr_simp |