 |
miasm
Reverse engineering framework
|
 |
miasm
Reverse engineering framework
|
Public Member Functions | |
| def | __init__ (self, ir_arch, state=None, sb_expr_simp=expr_simp_explicit) |
| def | get_state (self) |
| def | set_state (self, state) |
| def | eval_expr_visitor (self, expr, cache=None) |
| def | eval_exprint (self, expr, **kwargs) |
| def | eval_exprid (self, expr, **kwargs) |
| def | eval_exprloc (self, expr, **kwargs) |
| def | eval_exprmem (self, expr, **kwargs) |
| def | eval_exprcond (self, expr, **kwargs) |
| def | eval_exprslice (self, expr, **kwargs) |
| def | eval_exprop (self, expr, **kwargs) |
| def | eval_exprcompose (self, expr, **kwargs) |
| def | eval_expr (self, expr, eval_cache=None) |
| def | modified (self, init_state=None, ids=True, mems=True) |
| def | dump (self, ids=True, mems=True) |
| def | eval_assignblk (self, assignblk) |
| def | apply_change (self, dst, src) |
| def | eval_updt_assignblk (self, assignblk) |
| def | eval_updt_irblock (self, irb, step=False) |
| def | run_block_at (self, ircfg, addr, step=False) |
| def | run_at (self, ircfg, addr, lbl_stop=None, step=False) |
| def | del_mem_above_stack (self, stack_ptr) |
| def | eval_updt_expr (self, expr) |
| def | mem_read (self, expr) |
| def | mem_write (self, dst, src) |
Public Attributes | |
| expr_to_visitor | |
| symbols | |
| ir_arch | |
| expr_simp | |
Static Public Attributes | |
| StateEngine = SymbolicState | |
Properties | |
| state = property(get_state, set_state) | |
Symbolic execution engine
Allow IR code emulation in symbolic domain
Examples:
from miasm.ir.symbexec import SymbolicExecutionEngine
from miasm.ir.ir import AssignBlock
ir_arch = ir_x86_32()
init_state = {
ir_arch.arch.regs.EAX: ir_arch.arch.regs.EBX,
ExprMem(id_x+ExprInt(0x10, 32), 32): id_a,
}
sb_exec = SymbolicExecutionEngine(ir_arch, init_state)
>>> sb_exec.dump()
EAX = a
@32[x + 0x10] = a
>>> sb_exec.dump(mems=False)
EAX = a
>>> print sb_exec.eval_expr(ir_arch.arch.regs.EAX + ir_arch.arch.regs.ECX)
EBX + ECX
Inspecting state:
- dump
- modified
State manipulation:
- '.state' (rw)
Evaluation (read only):
- eval_expr
- eval_assignblk
Evaluation with state update:
- eval_updt_expr
- eval_updt_assignblk
- eval_updt_irblock
Start a symbolic execution based on provisioned '.ir_arch' blocks:
- run_block_at
- run_at
| def miasm.ir.symbexec.SymbolicExecutionEngine.__init__ | ( | self, | |
| ir_arch, | |||
state = None, |
|||
sb_expr_simp = expr_simp_explicit |
|||
| ) |
Reimplemented in ctype_propagation.TypePropagationEngine, and miasm.analysis.cst_propag.SymbExecState.
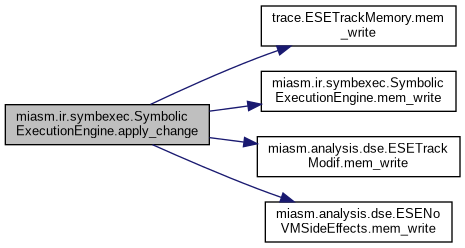
| def miasm.ir.symbexec.SymbolicExecutionEngine.apply_change | ( | self, | |
| dst, | |||
| src | |||
| ) |
Apply @dst = @src on the current state WITHOUT evaluating both side @dst: Expr, destination @src: Expr, source
Reimplemented in miasm.ir.symbexec_types.SymbExecCType, miasm.ir.symbexec_top.SymbExecTopNoMem, and miasm.analysis.dse.ESETrackModif.
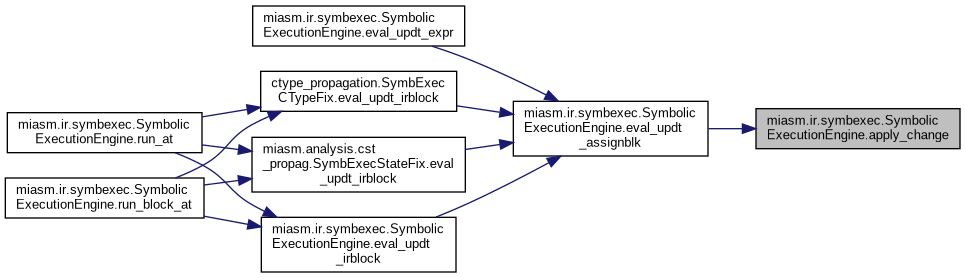
| def miasm.ir.symbexec.SymbolicExecutionEngine.del_mem_above_stack | ( | self, | |
| stack_ptr | |||
| ) |
Remove all stored memory values with following properties: * pointer based on initial stack value * pointer below current stack pointer
Reimplemented in miasm.ir.symbexec_types.SymbExecCType.
| def miasm.ir.symbexec.SymbolicExecutionEngine.dump | ( | self, | |
ids = True, |
|||
mems = True |
|||
| ) |
Display modififed variables @ids: display modified ids @mems: display modified memory

| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_assignblk | ( | self, | |
| assignblk | |||
| ) |
Evaluate AssignBlock using the current state Returns a dictionary containing modified keys associated to their values @assignblk: AssignBlock instance
Reimplemented in miasm.ir.symbexec_types.SymbExecCType.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_expr | ( | self, | |
| expr, | |||
eval_cache = None |
|||
| ) |
Evaluate @expr @expr: Expression instance to evaluate @cache: None or dictionary linking variables to their values
Reimplemented in miasm.ir.symbexec_types.SymbExecCType, and miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_expr_visitor | ( | self, | |
| expr, | |||
cache = None |
|||
| ) |
[DEV]: Override to change the behavior of an Expr evaluation. This function recursively applies 'eval_expr*' to @expr. This function uses @cache to speedup re-evaluation of expression.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprcompose | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprCompose using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprcond | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprCond using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprid | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprId using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprint | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprInt using the current state
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprloc | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprLoc using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprmem | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprMem using the current state This function first evaluate the memory pointer value. Override 'mem_read' to modify the effective memory accesses
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprop | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprOp using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_exprslice | ( | self, | |
| expr, | |||
| ** | kwargs | ||
| ) |
[DEV]: Evaluate an ExprSlice using the current state
Reimplemented in miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_updt_assignblk | ( | self, | |
| assignblk | |||
| ) |
Apply an AssignBlock on the current state @assignblk: AssignBlock instance
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_updt_expr | ( | self, | |
| expr | |||
| ) |
Evaluate @expr and apply side effect if needed (ie. if expr is an assignment). Return the evaluated value
| def miasm.ir.symbexec.SymbolicExecutionEngine.eval_updt_irblock | ( | self, | |
| irb, | |||
step = False |
|||
| ) |
Symbolic execution of the @irb on the current state @irb: irbloc instance @step: display intermediate steps
Reimplemented in miasm.analysis.cst_propag.SymbExecStateFix, and ctype_propagation.SymbExecCTypeFix.
| def miasm.ir.symbexec.SymbolicExecutionEngine.get_state | ( | self | ) |
Return the current state of the SymbolicEngine
Reimplemented in miasm.ir.symbexec_types.SymbExecCType, and miasm.ir.symbexec_top.SymbExecTopNoMem.
| def miasm.ir.symbexec.SymbolicExecutionEngine.mem_read | ( | self, | |
| expr | |||
| ) |
[DEV]: Override to modify the effective memory reads Read symbolic value at ExprMem @expr @expr: ExprMem
Reimplemented in miasm.jitter.emulatedsymbexec.EmulatedSymbExec, miasm.analysis.dse.ESETrackModif, and trace.ESETrackMemory.
| def miasm.ir.symbexec.SymbolicExecutionEngine.mem_write | ( | self, | |
| dst, | |||
| src | |||
| ) |
[DEV]: Override to modify the effective memory writes Write symbolic value @src at ExprMem @dst @dst: destination ExprMem @src: source Expression
Reimplemented in miasm.analysis.dse.ESENoVMSideEffects, miasm.analysis.dse.ESETrackModif, miasm.jitter.emulatedsymbexec.EmulatedSymbExec, and trace.ESETrackMemory.
| def miasm.ir.symbexec.SymbolicExecutionEngine.modified | ( | self, | |
init_state = None, |
|||
ids = True, |
|||
mems = True |
|||
| ) |
Return the modified variables. @init_state: a base dictionary linking variables to their initial values to diff. Can be None. @ids: track ids only @mems: track mems only
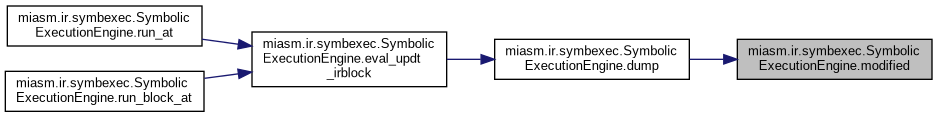
| def miasm.ir.symbexec.SymbolicExecutionEngine.run_at | ( | self, | |
| ircfg, | |||
| addr, | |||
lbl_stop = None, |
|||
step = False |
|||
| ) |
Symbolic execution starting at @addr @addr: address to execute (int or ExprInt or label) @lbl_stop: LocKey to stop execution on @step: display intermediate steps
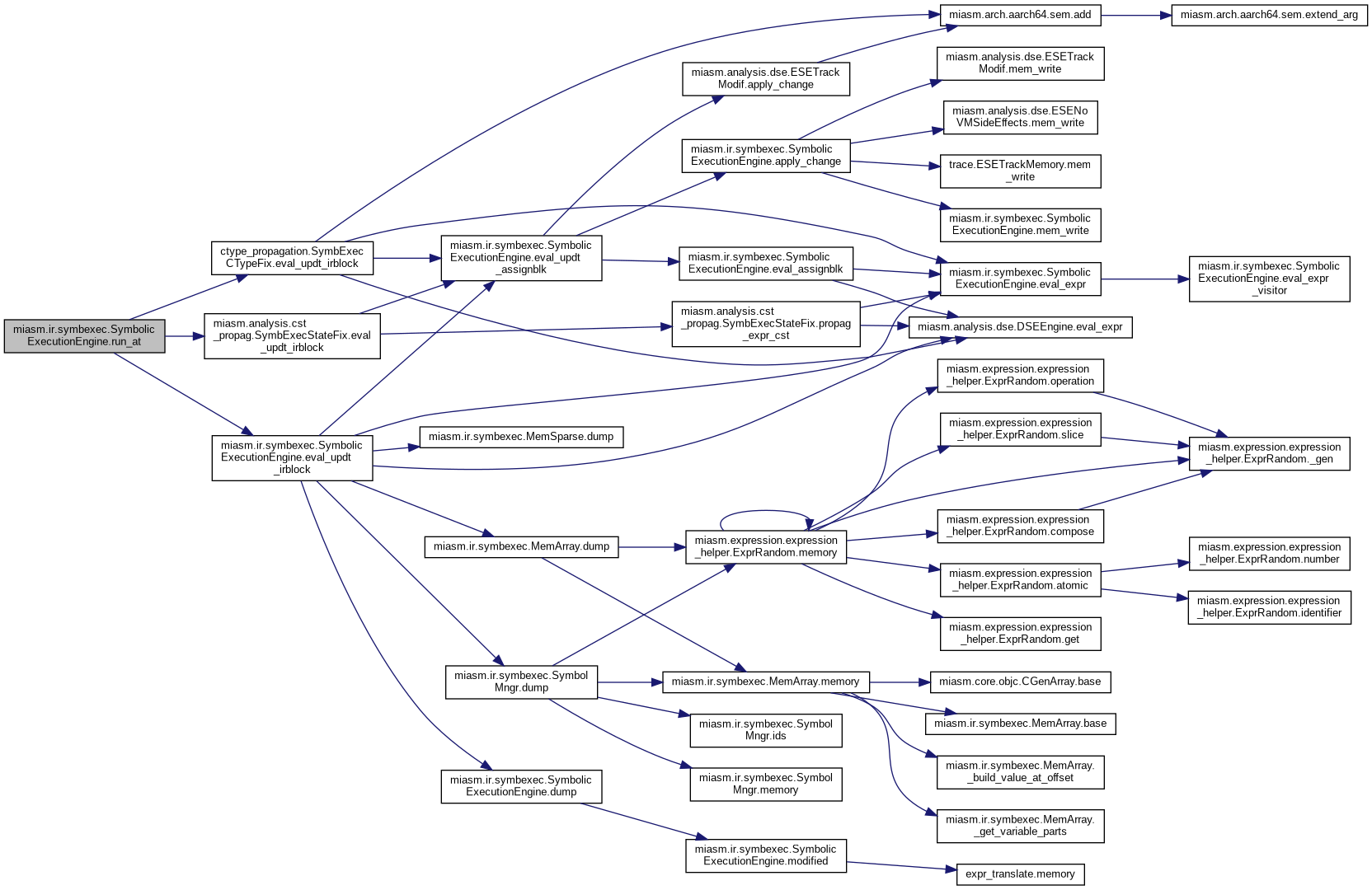
| def miasm.ir.symbexec.SymbolicExecutionEngine.run_block_at | ( | self, | |
| ircfg, | |||
| addr, | |||
step = False |
|||
| ) |
Symbolic execution of the block at @addr @addr: address to execute (int or ExprInt or label) @step: display intermediate steps
| def miasm.ir.symbexec.SymbolicExecutionEngine.set_state | ( | self, | |
| state | |||
| ) |
Restaure the @state of the engine @state: StateEngine instance
| miasm.ir.symbexec.SymbolicExecutionEngine.expr_simp |
| miasm.ir.symbexec.SymbolicExecutionEngine.expr_to_visitor |
| miasm.ir.symbexec.SymbolicExecutionEngine.ir_arch |
|
static |
| miasm.ir.symbexec.SymbolicExecutionEngine.symbols |